Darren, g0hww has attempted to persuade me several times over the last year or two that I really needed to try some of the devices from Pycom.
I resisted for quite a while, but finally broke a few weeks ago. I was looking out at our Polytunnel while it was raining and was wondering what the temperature was in the tunnel. Sure, I could walk out in the rain and check on the thermometer, but that would require effort, and the potential to get wet etc.
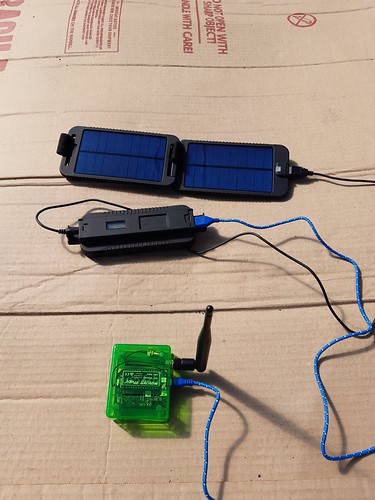
So I caved, and ordered some Lopy4’s and accessories including a Pysense 2.0X.
Darren gave me a copy of his code for his own project, and after some bodging (principally around getting the deep sleep to work correctly), I had enough done for an initial deployment.
I used my Powermonkey Extreme from powertraveller.com to power it up and left it run over night. On checking it the following morning, I was slightly surprised and disappointed at how quickly the Powermonkey battery seemed to drop given the LoPy4 shouldn’t be using all that much power from the power bank(33.3WH), however the low temperatures are probably a major factor in this. The power consumption is approximately 0.95 of an hour at 13mA and 0.05 of an hour at 130mA, which comes to about 20mAh or about 0.1Wh at 5 Volts.
After looking around my ‘stores’ I found some other bits to make the deployment it a bit more practical. A recycled 12v PV panel and Victron Bluesolar PWM Light Charge Controller (thanks @floatsam for both of those), a recycled 7Ah SLA from a decommissioned UPS in work, and a DC/DC converter.
It worked very well at this location, but now it was in danger of getting watered along with some seedlings, so it had to move. A few screws, a bit of board and some Galvoband, and he-presto a new shelf.
The LoPy itself is close enough to the house that WiFi is working fine, no need for LoRa. So I spun up a Virtual Machine on my Proxmox server, installed a Mosquitto MQTT Broker, bodged some more Python, threw in a bit of influxdb, grafana and pushover. And now, as well as having some nice graphs, I’ll get an alert if the temperature goes to high or too low.
Success!